Content Delivery Network (CDN)
Content distribution network (CDN) is a large distributed system of servers which are deployed in multiple data centers across the Internet. CDNs serve a large fraction of the Internet content today. This include Web objects like text, graphics and scripts, or downloadable objects such as media files, software, documents, or applications like e-commerce, portals, live streaming media, on-demand streaming media, and social networks. The goal of a CDN is to serve content to end users with high availability and high performance. CDNs also offload the traffic served directly from the content provider’s origin infrastructure, resulting in cost savings for the content provider, besides its better performance and availability.
Most important security issue is that CDNs provide the content provider a degree of protection from Denial of Service (DoS) attacks by using their large distributed server infrastructure to absorb the attack traffic. The most famous example today of using the CDN is that the need for some library to build a traditional website. For example, better performance can be achieved when loading a jquery.js library from a CDN, such as the one provided by Google. CDN provides high bandwidth and high performance content delivery.
An increasing number of Internet network owners have built their own CDNs to improve on net content delivery, reduce demand on their own telecommunications infrastructure, and to generate revenues from content customers. Most CDNs are operated as an Application Service Provider (ASP) on the Internet which also known as on-demand software or software as a service. Some larger software companies such as Microsoft build their own CDNs in tandem to their own products. Examples include Windows Azure CDN and Amazon CloudFront, there are many benefits for using CDN, such as:
- Fast using a network of edge locations around the world.
- Simple, a single API calls lets user get started distributing content from CDN to any other applications.
- CDN is designed for use with other custom Web services.
- Cost effective, through scaling user requirement, user pay only for the content delivered through the network.
- Elastic, users don’t need to worry about maintaining expensive Web server capacity to meet the demand from potential traffic spikes for their content.
- Reliable, CDN is built using highly reliable infrastructure, the distributed nature of edge locations used by CDN automatically routes end users to the closest available location as required by network conditions. CDN constantly monitors and optimizes for both availability and performance.
- Global CDN uses a global network of edge locations, located near your end users in the United States, Europe, Asia, and South America.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”
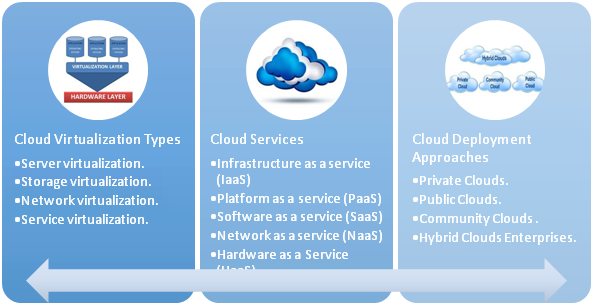
Cloud Virtualization Types
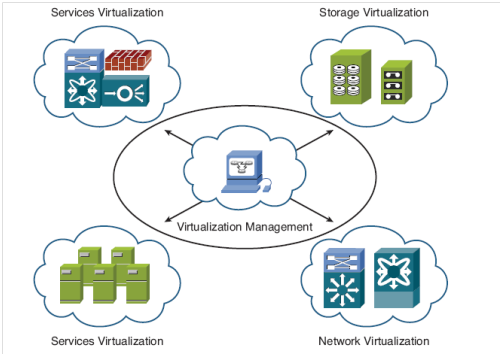
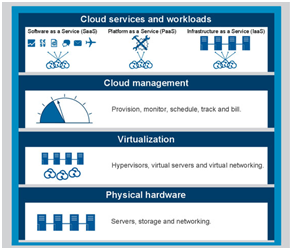
Many-to-one virtualization enables the creation of virtual or logical resources from multiple physical resources. This is the core context of cloud computing in which multiple physical resources are grouped together to form one cloud. Virtualization refers to OS virtualization as administrators can implement it by VMware, Xen, or other hypervisor-based technologies. Virtualization is not cloud, rather an enabler for establishing and managing clouds. In the Cisco cloud concept, virtualization is extended to incorporate various types of virtualization, such as network, computer, storage, and services. Generally, there are five varieties of cloud services and four types of deployment approaches, Figure 1.1 illustrates these concepts.
Virtualization is useful for several purposes such as sharing a computer system among multiple users, isolating users from each other, and emulating hardware on another machine. Figure 1.2 illustrates the virtualization types.
Server virtualization
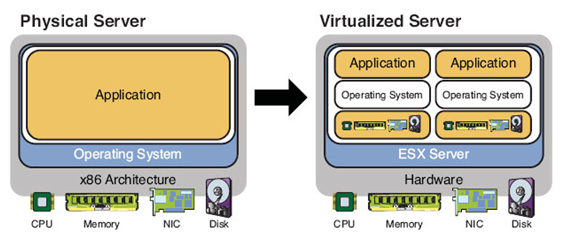
Hardware virtualization or server virtualization is the best known application for hardware virtualization. Server virtualization changes the rules by breaking the traditional model of one physical server playing host to a single operating system by creating several virtual machines on top of a single server using hypervisor technology. Computer hardware was designed to run a single operating system and a single application, this leaves most machines vastly underutilized. Virtualization lets the users run multiple virtual machines on a single physical machine, sharing the resources of that single computer across multiple environments. Figure 1.3 illustrates the differences between the physical server and the virtual server.
In a traditional server model, there is a single OS image for each machine, software and hard ware are tightly coupled, multiple applications often conflict, and there is a single IP address for each server. In virtualization, there is a separation of OS and hardware, OS and application contained in a single virtual machine (VM), applications are isolated from one another, hardware independence, and virtual IP address for each VM. Following are the advantages of server virtualization:
- Partitioning
- Single physical machine can run multiple operating systems on it.
- Divide the physical system resources among virtual machines.
- Each VM work independent and does not know the presence of the other.
- Management
- Failure of one VM does not affect other VMs.
- Each VM could be management separately and there is individual performance for each VM.
- Encapsulation
- The state of any VM can be saved in a file.
- Easy moving and copying VM files information.
- Flexibility
- Allows provisioning and migration of any VM to a similar machine on any physical server.
- Usage of multiple OS platforms, for example, Windows, Linux.
- Allows VM configuration changes without actually bringing the VM down.
Storage virtualization
Storage virtualization refers to providing a logical, abstracted view of physical storage devices. It provides a way for many users or applications to access storage without being concerned with where or how that storage is physically located or managed. Storage systems may use virtualization concepts as a tool to enable better functionality and more advanced features within and across storage systems. Storage virtualization enables physical storage to be shared across multiple application servers. Physical devices behind the virtualization layer can be viewed and managed as if they are one large storage pool with no physical boundaries. The storage virtualization makes multiple separate storage devices appear as one device
Virtualization hides the complex process of where the data needs to be stored and bringing it back and presenting it to the user when it is required. Storage Area Network (SAN) arrays use this concept of storage virtualization. SANs enables scalable and flexible storage resource allocation, efficient backup solutions, and higher storage utilization. Storage virtualization provides the following benefits:
- Resource optimization.
- Cost of operation.
- Increased availability.
- Improved performance.
- Simpler data migration and mobility.
- Development of a service catalog.
- Ability to monitor capacity utilization and performance.
- Signification cost savings.
Network virtualization
Network virtualization is the process of combining hardware and software network resources and network functionality into a single software based administrative entity for virtual network, or mapping two or more disparate networks into a single network. This concept enables the deployment of different architectures and protocols over a shared physical infrastructure and makes it look as if all remote networks are in a single place. The goal of network virtualization is to provide systems and users with efficient, controlled, and secure sharing of the networking resources. Network virtualization involves platform virtualization, often combined with resource virtualization, and it is true that the final product of network virtualization is the virtual network.
Virtual networks are classified into two broad types, external and internal. External virtual networks consist of several local networks that are administered by software as a single unit. The main components of classic external virtual networks are switch hardware and VLAN software technology. Examples of external virtual networks include large corporate networks and data centers. The internal virtual network consists of one system using virtual machines or zones that are configured over at least one pseudo network interface. These containers can communicate with each other as though on the same local network, providing a virtual network on a single host. The building blocks of the virtual network are Virtual Network Interface Cards or Virtual NICs (VNICs) and virtual switches.
Components of a virtual network
- Network hardware, such as switches and network interface cards (NICs).
- Network elements such as firewalls and load balancers.
- Networks, such as virtual LANs (VLANs) and containers such as virtual machines.
- Network storage devices.
- Network M2M elements such as telecommunications 4G HLR and SLR devices.
- Network mobile elements such as laptops, tablets, and cell phones.
- Network media, such as Ethernet and Fiber Channel.
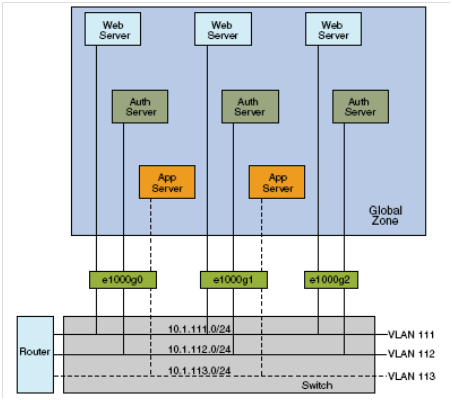
It is possible to configure multiple virtual networks within a single network unit, for example a switch using VLANs. Figure 1.4 illustrates a system with three physical NICs without VLANs, the user would configure different systems to perform specific functions and connect these systems to separate networks. For example, Web servers would be connected to one LAN, authentication servers to another, and application servers to a third network. With VLANs and zones, the user can collapse all eight systems and configure them as zones in a single system. Hence, uses VLAN tags, or VLAN IDs to assign a VLAN to each set of zones that performs the same functions.
Service virtualization
In the cloud world where almost everything is a service, the thinking of cloud computing as the transformation of computing that brings together service orientation with distributed manageability combined with the economies of scale from virtualization is imminent. Service virtualization is a fundamental mechanism for delivering services. Service virtualization in data centers refers to the services such as firewall services for additional security or load-balancing services for additional performance and reliability. Service virtualization is considered as a method to emulate the behavior of specific components in heterogeneous component based applications such as service oriented architectures.
Service Oriented Architecture (SOA) is a software design and software architecture design pattern based on structured collections of discrete software modules, known as services that collectively provide the complete functionality of large software application. SOA allow easy cooperation of a large number of computers that are connected over a network. Every computer can run an arbitrary number of programs which is called services in a context that are built in a way to exchange information with any other service. Within the reach of the network without human interaction and without the need to make changes to the underlying program itself.
The virtual interface, often referred to as a Virtual IP (VIP), is exposed to the outside world, representing itself as the actual Web server, and manages the connections to and from the Web server as needed. This enables the load balancer to manage multiple Web servers or applications as a single instance, providing a more secure and robust topology than one allowing users direct access to individual Web servers. This is a one-to-many virtualization representation. One server is presented to the world, hiding the availability of multiple servers behind a reverse proxy appliance.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”
Cloud Deployment Approaches
Cloud computing services are offered through some cloud deployment approaches. Cloud deployment service can be classified into four main types, public, private, community, or hybrid. Cloud framework begins with the physical hardware of the cloud. The virtualization layer comes above the hardware layer, the next layer is the cloud management layer, and the final layer is the cloud services layer which is deployed by the cloud providers to make the cloud provisions available to the cloud consumers such as IaaS, PaaS and SaaS. Figure 1.1 illustrates this concept.
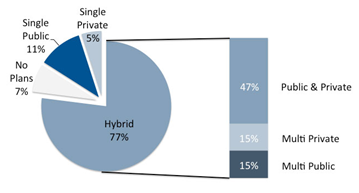
Cloud deployment models used to power the organization to provide services to its customers, choosing the deployment model is one of the biggest challenges that face any organization. One of the most common strategies is the public cloud services for development and test or less critical applications, allocating business critical applications to a more enterprise class cloud and running their mission critical apps on an in house cloud. Following is a discussion of the deployment types. Figure 1.2 illustrates the current percentage for each of these types.
Private Clouds
When there is an internal data centers of a business or organization and is not made available for the public, it is called a private cloud. Sometimes private cloud named as an internal cloud and this type of cloud exists within the boundaries of an organization. Private cloud is a computing platform or architecture that provides hosted services to a limited number of people behind a firewall. The infrastructure for private cloud is operated solely for a single organization, but it managed internally by a third-party that hosted internally or externally. The virtualization and distributed computing is required to setup a private cloud project, this makes the organization reevaluate decisions about existing resources. Organizations should buy, build, and manage the hardware and software by themselves.
Private cloud is designed to offer the same features and benefits of public cloud systems, but removes a number of objections to the cloud computing model including control over enterprise and customer data due to worries about security and issues connected to regulatory compliance. Because a private cloud setup is implemented safely within the corporate firewall, the implementation is aimed to avoid many of the objections regarding cloud computing security. A private cloud provides more control over the company’s data and ensures security, albeit with greater potential risk for data loss due to natural disaster. When an organization implements the private cloud, it is responsible for running and managing the IT resources instead of passing this responsibility on to a third-party cloud provider.
Public Clouds
Public cloud is a computing environment that consists of a set of computers and computer network resources based on the standard cloud computing model that is open for use to the public. Public cloud is a cloud services provided by third parties but hosted and managed by the service providers. The infrastructure is owned by an organization that sale the cloud services to the general public or to a large industry group. Using public cloud, users could delegate all service management and support to the service provider who is taking the responsibility of installation, management, provisioning, and maintenance. Applications, storage, and other resources are made available to the general public by the service provider. Public cloud customers only access and use the services and physical resources and they are charged for the used resources and services only.
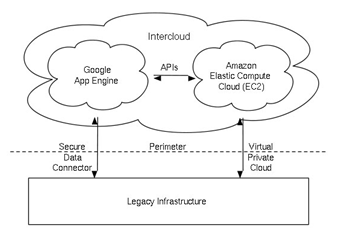
There is a special type of deployment model called Virtual Private Cloud (VPC) that comes to exist when the service provider uses public cloud resources to develop a private cloud environment. Users can create a VPC as configurable pool of shared computing resources allocated within a public cloud environment. Figure 1.3 illustrates the way to create virtual private cloud. The cloud provider usually choose the hardware and the cloud users cannot do this like in the private cloud. The virtualization and device independence is very clear in this type, so the public cloud can be described as an external cloud when viewed from within a given organization.
Community clouds
When sharing infrastructure between several sites and organizations with common issues such as security, compliance, etc., this is called a community cloud. It is hosted internally or externally and could be managed internally or by a third party. The cost is spread over fewer users than a public cloud, only some of the cost savings potential of cloud computing are realized. Community cloud is best when looking for energy, cost efficiency, and vertical applications. Any software that support specific business processes to targets a smaller number of users within an organization called a vertical application. Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM) are examples of vertical applications.
All kinds of underutilized and unutilized computing machines are being networked, clustered, and virtualized to act as a community cloud that is capable of effortlessly to tackle specific needs of a particular community. Community cloud offers an alternative architecture for the use cases of cloud computing. The community cloud is not owned or controlled by one organization, and therefore not dependent on the lifespan or failure of any one organization. It is resilient to failure and robust, with no system wide cascade failures, because of the diversity of its supporting nodes. Community cloud offer control convenience because its community ownership provides for democratic distributed control. Community cloud makes use of underutilized user machines that require much less energy than the dedicated data centers required for vendor Clouds.
Hybrid Clouds Enterprises
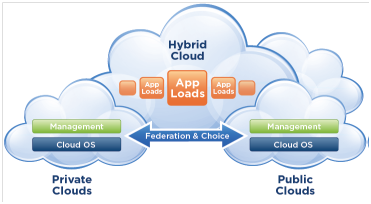
The combination of private, community, and/or public clouds are called hybrid clouds. This composition of two or more clouds offers the benefits of multiple deployment models. This type of composition expands deployment for could services and allow organizations to use public cloud resources to meet temporary needs. This allows hybrid cloud to enable cloud bursting for scaling across clouds. The common big misperception is that cloud computing implies an external cloud, based on public cloud services. But the fact is that cloud computing is how to approach information technology. It is a way of doing computing, not a destination. Most enterprises will benefit from adopting cloud computing within their own data centers building which is a private clouds, and getting there in an evolutionary way through their existing virtualization technology. Figure 1.4 illustrates how hybrid cloud infrastructure works.
Cloud bursting is an application deployment model in which an application runs in a private cloud or data center and bursts to a public cloud when the demand for computing capacity increases. Primary advantage of cloud bursting and a hybrid cloud model is that an organization only pays for extra compute resources when needed. Cloud bursting enables data centers to create an in house IT infrastructure that supports average workloads and use cloud resources from public or private clouds during spikes in processing demands. A high degree of fault tolerance combined with locally immediate usability is obtained when using hybrid cloud architecture without depending on Internet connectivity. Hybrid cloud architecture requires both on premises resources and off site or remote server based cloud infrastructure. Hybrid cloud provides the flexibility of in house applications with the fault tolerance and scalability of cloud based services.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”
Planning the Structure of Your Mobile Web Site
While structuring a mobile website, we must spend enough time on information architecture design, if the user has to spend too much time to locate the information he/she wants, they may get bugged and go away, no businessman or even normal user would like that, all web site owners certainly not going to allow that, here is some guide lines we should follow them:
- Define user personas: Who is going to use the web site? What’s the target market? In what circumstances will they come to the site? What’s the context? List down typical users who would use the application.
- Define user goals: What tasks do they want to achieve on the web site? Is there a better way of achieving these goals than a typical website flow? Why would they want to do this task over a mobile? How does your mobile site help them accomplish their goals?
- Define target devices: Do you want to limit to a particular set of devices? Or use some device-specific feature? Do you want to use SMS/Phone capabilities?
- Do paper prototypes: Sketch out the workflow for accomplishing user goals on paper (yes, pen and paper are still useful!).
- Test with real users: Show the prototype to real users and get their feedback, Make modifications, accordingly.
- Make XHTML prototype and test again: After you’ve passed the paper prototyping round, convert the prototypes into XHTML MP. Now test them on target mobile devices. Test them also with real users and make modifications till you get things right.
Here are also a few tips you can keep in mind when you work on your mobile websites:
- Take a minimum approach, remove everything that you can.
- Respect the user’s time, money, and attention. Don’t frustrate them.
- Do task centered design and focus on user goals.
- Give less choice no long menus, no long options, and no long pages.
- Maximum 10 links on a page.
- Navigation should be drill down, and contextual. Customize navigation, according to the page, no more than 5 levels of drilling down.
- No pages with just links to drill down further, make sure each page has valuable content. Even the homepage should have actionable content.
- Prioritize links and content. What’s more important goes to the top.
- Always provide a way to exit to home, and step back in the footer.
- Break lengthy/complicated forms into a wizard like step-by-step process.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”
Website Design Service for Mobile Devices
Accessing the Internet from mobile devices is becoming increasingly popular, for the past few years mobile devices (mobile phone, smart phone, tablets, PDA or palmtop) have rapidly become an integral part of our lives, We can talk and send messages or video streams by them, and with an internet connection we can have access to any kind of web content, Today there are over 1.1 billion web capable handsets in use worldwide which is 63% of the total handsets of the world, However, as can be read in mobile web access is hindered by the fact that the majority of web contents are tailored for desktop computers. Compared to desktop computers mobile devices have got some evidential drawbacks.
Web access from mobile devices presents its own unique challenges we have to severe resource constraints on the mobile devices, their performance is usually much lower processor memory, their screens are smaller, and generally their internet connections are much slower, power, form factor, bandwidth and battery, mobile web users face a big problem that the majority of web content are tailored for desktop computers which can have a large display area and high connection speed compared with mobile devices which have smaller display area and limited connection speed also, There was many trials to solve this problem or even enhance the existing model to have better results.
Hence in the majority of the cases it is impossible to display the original web content, which is customized to a desktop computer with a 17” monitor or higher, on the display of a handheld device in a usable and efficient way. Somehow we should adapt the original content to the capabilities of the client device. This problem led to create two versions from any web content one for desktop computer and other with special constrains for mobile web. There were some others contributions to solve this problem, Instead of having two versions for each web content one for normal users and the other for mobile users.
Also there is an important issue should take in consideration when you author any web content that we should optimize it we will list some best practices for delivering web content to mobile devices to save mobile resources like battery power and limited connection speed, The principal objective is to improve the user experience of the web when accessed from such devices, and also use some technique to the Hypertext Transfer Protocol (HTTP) request and improve the display of the same content to fit the mobile users.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”
What is Mobile Web Limitations?
Old mobile devices have screen size from 120×120 pixels up to 320×240 this means that you can show about 6 lines of 25 characters, some mobiles also support a few types of images and multimedia format for example animated GIF is not supported on most phones, the mobile browser of course faces the same limitations that mobile web faces like:
- Small screen size: This makes it difficult or impossible to see text and graphics dependent on the standard size of a desktop computer screen.
- Lack of windows: Ability to open more than one window
- Navigation: No mouse thereby limiting the flexibility in navigation
- Lack of JavaScript and cookies: Most devices do not support client-side scripting and storage of cookies except smart phones and iPhone, this is not being suitable for uniquely identifying visitors using mobile devices.
- Speed: Most mobile devices speed of service is very slow, often slower than dial-up Internet access.
- Types of pages content like (Flash, PDF …)
- Compressed pages
- Size of messages: Many devices have limits on the number of characters that can be sent in an email message.
- Cost: Access and bandwidth charges levied by cell phone networks are much higher than those for fixed-line internet access.
Now day mobile devices try to solve most of the previous problems thought develop some strategies like increasing the screen size, enhance the hard resources like processor capability, add more ram, develop a new operating system (OS), enhance the Global System for Mobile Communications (GSM) network itself or add a network card to provide the wireless access thought using the Wi-Fi technology.
OneHoster is one of the best web hosting companies in Egypt, we offer many web hosting packages in Egypt and middle east like, cPanel storage hosting packages, cloud hosting, domain registration, dedicated servers solution, Email hosting, WordPress hosting, web hosting upgrades and hosting renewals to suit your requirements to host your website for small and medium sized businesses. OneHoster is also one of the top 10 website design companies, and top 10 digital marketing companies in Egypt and Middle east.
“OneHoster’s Team”